为什么 TPM 可以防重放

TPM 芯片使用过程中,涉及到类似身份认证的事情,例如:
- TPM 命令使用口令/ Policy
- TPM Hash 签名
- TPM 身份证书 AK、EK、PK 等
在使用 TPM 相关功能的时候会考虑一个问题,如果攻击者拿着一个伪造的数据作为 TPM Command 的输入,是否能够绕过检查机制即怎么防止重放攻击。TCG 在设计 TPM spec 的时候就考虑了这问题,TCG 将 TPM 涉及到的数据分为两种类型:1. TPM 内部生成的数据;2. TPM 外部生成的数据,这篇文章会从数据类型的角度介绍 TPM 本身防重放攻击的原理。
内部数据防重放
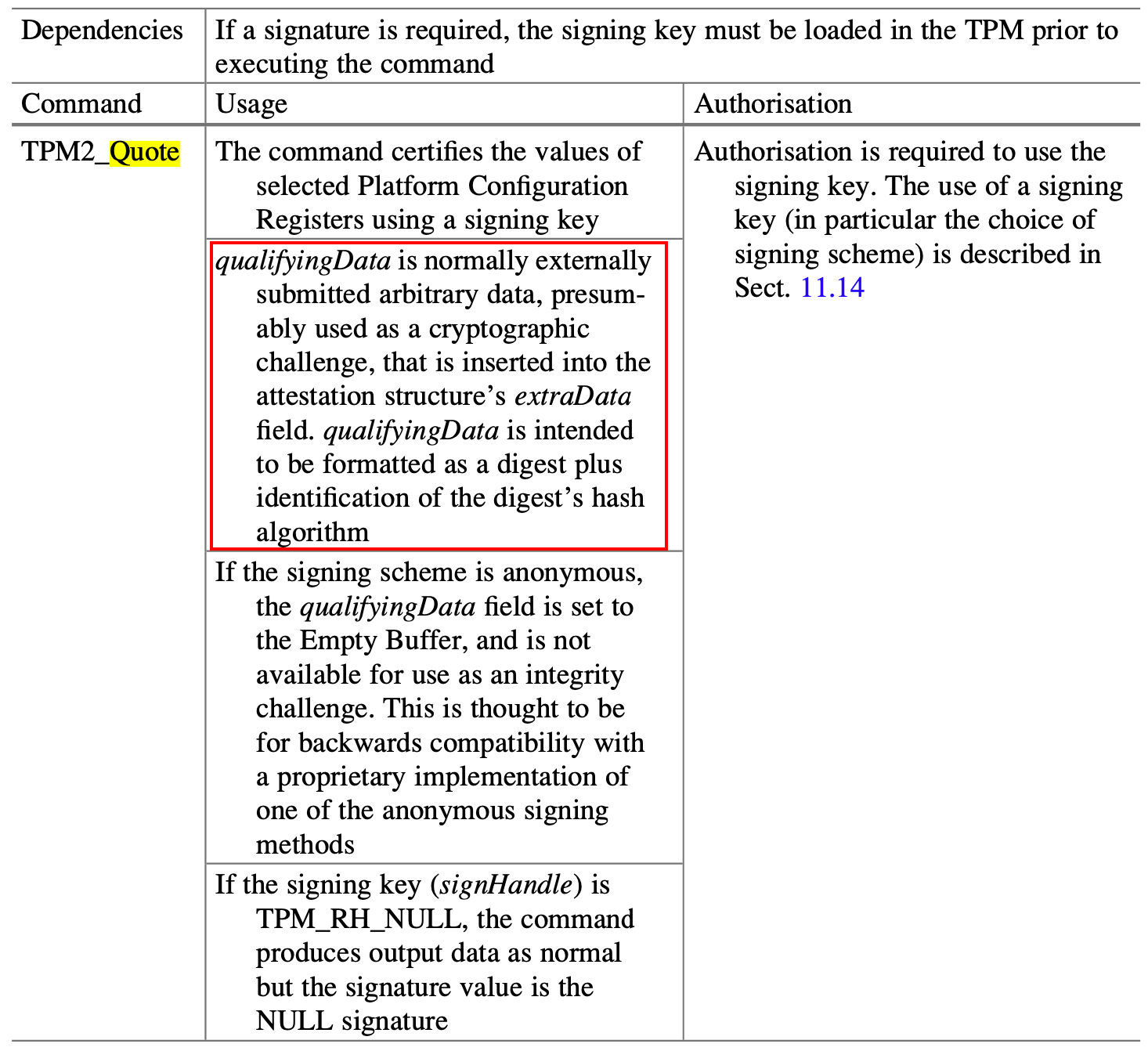
TPM 内部数据主要是通过外部给定随机数 nonce 值的方式来抵御重放攻击,以 TPM2_Quote 命令为例,在引用 PCR 值作为Quote 数据结构体的时候需要指定 qualifyData。
外部数据防重访
TPM 对于外部数据主要是通过要求提供 TPM 生成的 HMAC 签名来确认,外部数据是经过 TPM 认证保护的,里 TPM2_Sign/TPM2_Hash 为例:
- In order to determine whether external data mimics the TPM’s attestation structures,
TPM2_Signrequires the caller to provide verification evidence, which is aTPMT_TK_HASHCHECKticket (an HMAC signature) created by the commandTPM2_HashorTPM2_SequenceComplete.TPM2_Hashis quicker and easier thanTPM2_SequenceCompletebut can be used only when the external data fits in a single TPM buffer.TPM2_SequenceCompletecan verify arbitrarily large amounts of external data. - A verification ticket comprises evidence that the digest described by the ticket doesn’t start with the
TPM_GENERATED_VALUE = 0xFF'TCG (FF 54 43 47 16)header that appears in the TPM’s attestation structures. Tickets are succinctly described in TPM2 specification Part-1 section “Signature Opera- tions” subsection “Tickets”. - The verification ticket submitted with the
TPM2_Signcommand must be created by the same TPM that will execute theTPM2_Signcommand. The reason is that a ticket is signed by a secret value that is never known outside the TPM.


Public discussion